10 Common Security Mistakes Sysadmins Make & How To Avoid These Pitfalls

It is valuable to learn from any administrative mistakes you make rather than repeat the same issue again. System administrators, or sysadmins, make mistakes but utilize what they learn to develop more skills, advance their careers, and improve their capabilities. It's also helpful to learn from the blunders of others, so today, we will discuss ten common administrative mistakes sysadmins make and how to address such problems.
Overuse of Privilege Escalation

Sudo access permits users to control who runs commands on the system, as well as permits such users to do so with elevated privileges. Sysadmins can delegate permissions so workers can perform certain root commands and provide an audit record of actions and arguments.
Adversaries can escalate privileges by implementing poorly configured methods that take away the need for a password. It's easy for sysadmins to get frustrated every time workers require sudo access for a minor task, so rather than finding an alternative, a system administrator will grant permanent sudo access to specific programs for users. This gives workers a clear path to the root software so they can utilize interactive shells and write to file systems. However, these types of common administrative mistakes give threat actors more advantage should they be able to breach into a sudo-accessed area of a system.
A mitigation solution would be to implement privileged account management. Even if an attacker has terminal access, they must know the password to run anything in sudo-accessed files. Sysadmins can also restrict file and directory permissions by modifying files to require passwords so users with greater privileges cannot initiate dangerous processes.
Key Takeaways:
- Use privilege account management.
- Restrict files and directories.
- Avoid using sudo if you don't have to.
Use of Outdated Software

Many of us are guilty of postponing a software update. As a system administrator, this laziness can be detrimental to your organization. It is critical that sysadmins track security advisories and network security issues and install security updates as soon as they become available. Many servers have been affected because a year-old fix was never installed, and instead, these servers were compromised by a zero-day attack.
Cybersecurity vulnerabilities can result from a lack of proper security patching done in due time. Hackers can sometimes see the updated patches and use them to instigate attacks in network security for systems that haven't upgraded yet. Missing updates might not always be due to mismanagement but could be because it would damage a legacy app.
If it's a crucial server, a few minutes of downtime during a scheduled maintenance window is preferable to losing hours or days because the box has been effectively compromised due to a network security threat. Test patches as soon as they are issued and set up a schedule for releasing updates. Perhaps there are ways to quarantine the servers to limit risk or to adopt new technologies to lessen reliance on legacy services. Security patching can be a political minefield in real life. If a higher-ranking manager prohibits a system from being patched, make sure everyone understands the consequences of not doing so. Bring the issue to the attention of the proper stakeholders and management so that everyone works to mitigate such cyber security vulnerabilities and avoids making such common administrative mistakes.
Key Takeaways:
- Test patches as soon as they are available.
- Quarantine servers if you can't push a crucial update.
- Make sure that management understands the importance of the update.
Bad Password Management
 Although passwords are still one of the most secure ways of authentication available, they are one of various cyber security vulnerabilities at risk when misused. Password management is helpful in this situation, as it is a collection of guidelines to follow while saving and managing passwords to keep systems as secure as possible and prevent unwanted access that could result in network security issues.
Although passwords are still one of the most secure ways of authentication available, they are one of various cyber security vulnerabilities at risk when misused. Password management is helpful in this situation, as it is a collection of guidelines to follow while saving and managing passwords to keep systems as secure as possible and prevent unwanted access that could result in network security issues.
Servers are frequently set up with weak administrator credentials or the same password for other machines. Because many people still make this basic mistake, brute-force attacks utilizing common passwords work. This network security threat becomes much worse when numerous machines share the same password, making it one of these common administrative mistakes.
Sysadmins should utilize a key file instead of using the same root password on all computers. Each server should have a public key file, and the private key should be paired with the public key on the system admin's desktop.
Key Takeaways:
- Don't use the same root password on all machines. Use a key file instead.
- Make sure admin credentials are strong.
- Do not have a list of passwords stored in a text file.
Troubleshooting Incorrect VLAN Assignment
Sysadmins use Virtual Local Area Networks (VLANs) to segment and organize networks. Segmenting has several benefits, including greater security since devices can only connect with other VLAN systems, as those are the only ones visible to users. VLANs can aid in controlling broadcast traffic and the movement of end systems around a network.
Users will be sent to the wrong VLAN if not correctly configured in these common administrative mistakes. This is why sysadmins have to deal with difficulties like network devices being unable to connect to switch ports, failed device registration efforts, and the inability to connect the device to critical servers.
To ensure that the device has the right IP address, test the switch port. Check which VLAN is configured on that port using a VLAN tag and make the necessary modifications. With documentation, you can avoid having cybersecurity vulnerabilities within your VLAN settings. VLAN is frequently assigned to the wrong port due to a lack of communication. Sysadmins, for example, would never know that specific ports need to be adjusted to be compatible with new services if there was no documentation.
Key Takeaways:
- Reconfigure ports to support new services.
- Check switch configuration to validate new VLAN assignments.
- Test the port to see which VLANs are supported.
Monitoring Log Files for Tampering and Attack Signals
Log files keep track of what's going on behind the scenes, so if something goes wrong with a complex system, you can refer to a complete record of events that occurred before the failure. This record includes transactions, errors, and intrusions. An Advanced Persistent Threat (APT) in your organization or other attacks in network security could result in your log files, typically in the form of transaction issues.
Sysadmins keeping track of log files can increase the chance of catching and stopping an intruder before any severe damage can occur. Log filtering software can help you analyze the data and find relevant log messages to prevent persisting common administrative mistakes.
Key Takeaways:
- Write logs to two separate locations and compare hashes.
- Don't log passwords or failed passwords from logins.
- Use log-filtering software to help find relevant information.
IP Address Conflict
At any one time, one IP address is assigned to each device on a network by default. However, two devices sharing the same IP address can prevent users from connecting to a network. The default Dynamic Host Configuration Protocol (DHCP) configuration on your router could be to blame, as well as manual human error.
Having a good DHCP server on your network is critical to protect your devices from IP conflicts. Bad DHCP servers may contain cyber security vulnerabilities that cause IP conflicts by incorrectly assigning IP addresses to network devices during dynamic IP allocation.
Sysadmins should reconfigure the router to assign DHCP addresses to the top end of your subnet, leaving the static IP addresses out of the mix to avoid these common administrative mistakes.
Key Takeaways:
- Check IP conflicts that arise from DHCP servers.
- Check BYOD policies.
- Release and renew your IP address.
Preventing DNS Failures

The Domain Name System (DNS) is a decentralized and hierarchical naming system for identifying computers, services, and other resources accessible via the Internet or Internet Protocol networks.
DNS failure prevents users from accessing the internet and other critical applications. A failed connection request occurs when the client PC cannot resolve the server name with the server's IP address. Cache poisoning, DDoS, and DNS rebinding attacks in network security are some exploits that adversaries might use to induce DNS failure.
Workstations may be configured to use their DNS server for highly active networks, resulting in a DNS traversal to your ISP's servers and overloading the router. To directly access their DNS servers, sysadmins need to change the client's DHCP settings. Disable DNS recursion to prevent DNS poisoning attacks. Have a server that will activate in the event of the nameservers failure to ensure data and network security.
Key Takeaways:
- Properly configure DHCP settings.
- Be prepared with a DNS failover.
- Disable DNS recursion to prevent cache poisoning.
Not Using Security Audits Best Practices
A security audit is a thorough examination of your company's information system. Often, this examination  compares the security of your system to a checklist of industry best practices, externally defined standards, or federal regulations. The audit thoroughly examines all aspects of your IT infrastructure, including operating systems, servers, digital communication and sharing abilities, network security toolkits, apps, and data storage and gathering methods.
compares the security of your system to a checklist of industry best practices, externally defined standards, or federal regulations. The audit thoroughly examines all aspects of your IT infrastructure, including operating systems, servers, digital communication and sharing abilities, network security toolkits, apps, and data storage and gathering methods.
A security audit will give a roadmap of your organization's primary information cyber security vulnerabilities, identifying where it is meeting and where it is not fulfilling the requirements set forth by the organization. For firms that deal with individuals' sensitive and confidential data, security audits are essential for building risk assessment plans and mitigation measures.
On the market, there are a variety of Computer-Assisted Audit Techniques (CAATs) that can help sysadmins automate the audit process to help with common administrative mistakes. CAATs go through the processes of an audit regularly, looking for cybersecurity vulnerabilities and generating audit reports automatically.
Key Takeaways:
- Understand that audits are essential for security.
- Enlist a third-party auditor.
- Use CAATs to automate the audit process.
Poor SSH Key Management
SSH is a secure protocol commonly used to connect to Linux servers. By establishing a remote shell, it provides a text-based interface. All commands you enter in your terminal are transferred to the remote server and executed after you connect. Any commands you type into your terminal are transferred across an encrypted SSH tunnel and executed on your server for the length of your SSH session. SSH is used by sysadmins frequently alongside SSH keys.
Mismanagement of SSH keys exposes you to data and network security threats and puts you out of compliance with industry regulations. If your keys are lying around or you frequently hand them out to everyone, that's very bad for security. Having an improper key management setup could also affect compliance needs.
SSH key management is a set of network security toolkits, policies, and processes that enable sysadmins to safeguard and manage such digital key pairs to prevent future common administrative mistakes. Users can utilize secure shell keys to authenticate themselves to your network, servers, or other systems and securely transfer files without logging in every time.
Key Takeaways:
- Keep an eye on the SSH key rotation.
- SSH keys should be tied to a specific person rather than an account several people can access.
- Find and keep an inventory of all SSH keys.
Improperly Configured & Open Ports
Ports allow devices to communicate with one another. To perform their tasks, internet-facing services, and applications listen on ports for a connection from the outside. Communication between hosts via the internet is impossible wi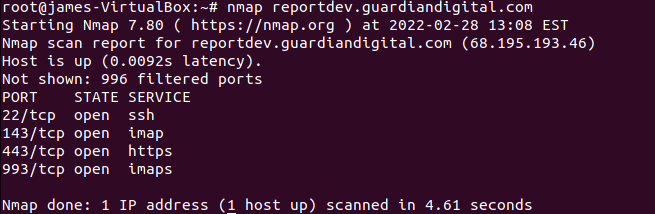 thout ports.
thout ports.
One of the most common administrative mistakes takes place when a port is left open when it should be closed. An administrator may have opened a port to fulfill a request and then forgotten about it, or a program may have automatically changed a firewall configuration, leaving some ports open without your knowledge.
Ports that aren't absolutely necessary should be closed as soon as possible to mitigate this network security threat. Sysadmins can also run port scans with network security toolkits like Nmap regularly.
Key Takeaways:
- Check for open ports with vulnerability scanners.
- After opening a port for requests, remember to close them.
- Check for ports that may have been opened from the firewall configuration.
Final Thoughts on Avoiding Common Administrative Mistakes as Sysadmins
Learning from others' mistakes can also be an invaluable tool to grow as a sysadmin without compromising company security in the process. In this article, we looked at ten common administrative mistakes that sysadmins make regarding security and tips for avoiding these pitfalls. We encourage you to explore this LinuxSecurity must-read article on top tips for securing your Linux system so that you can better protect your company against any and all cybersecurity vulnerabilities.
A common oversight by sysadmins involves underestimating the significance of a robust secure remote access solution. Thus, it is crucial to integrate a dependable remote access system which safeguards against unauthorized entries and counteracts potential threats from remote links, essential measures for ensuring network security.
Have you made any of these mistakes, or do you have additional advice for avoiding these issues? We'd love to discuss this with you!


















