How Can I Make PHP More Secure?

Organizations classify Hypertext Preprocessors (PHPs) as the most popular programming language since some of the biggest Internet names use the service in their businesses. PHPs help companies build websites, create applications, and manage their systems.
Although PHP is a powerful language that permits companies to explore their online potential, PHP is not the most secure option available, leaving organizations at risk of cloud security breaches, attacks, and other issues that could destroy a business’s reputation. Fortunately, there are solutions you can implement to strengthen your PHPs against any network security threat. This article will explain PHP’s relevance today, application pentesting, and best practices to utilize when mitigating attacks.
How Do Companies Use PHP for Security? Is It Still Relevant?
PHPs can still be helpful in security, as they can be relevant when appropriately used to determine what risks you might have in your system. Companies identify cybersecurity vulnerabilities using application pentesting software to simulate attacks in network security through the system. This type of privacy sandboxing can find flaws in company coding that could permit threat actors to take over websites and compromise sensitive data. This solution can find insecure coding, misconfigured settings, broken authentication controls, and information leaks. You can mitigate data and network security issues straightaway when using PHPs to combat hackers.
What Insecurities Do PHP Web Applications Have?
Some PHPs have Content Management Systems (CMS) built into the server as an extra level of protection in your system. To strengthen a company, PHPs implement CMS options like WordPress, Joomla, Magento, and Drupal. However, these services sometimes harbor cybersecurity vulnerabilities that allow cybercriminals to bypass security when you use this product. WordPress has network security issues that have increased vulnerabilities from seventy-four to eighty-three percent in just about a year. Fortunately, organizations consistently seek to improve the security posture options they provide to users to ensure they are safe to utilize for users.
How Can Application Pentesting Benefit Businesses?
As the name suggests, application pentesting focuses on identifying cybersecurity vulnerabilities in your web applications by inspecting your server for necessary patching in cybersecurity. Pentesting can find flaws in coding that could permit attackers to breach your system and steal credentials or data. With this privacy sandboxing technique, you can learn about misconfigurations, broken authentications, access control weaknesses, information leaks, and more within your company. Once you know the risk, you can remediate these exploits in cybersecurity before threat actors get their hands on them.
What PHP Best Practices Should I Employ to Strengthen Security?
1. Always use the latest version of PHP
Use the latest PHP version since it will be up-to-date with the latest security news so your company can have the features it needs to strengthen online security.
2. Properly configure the PHP.ini file and other requisites
Here is how you can tailor your system to your needs by starting with these configurations:
session.save_path
session.cookie_path (e.g. /var/www/mysite)
session.cookie_domain
 After configuring those settings properly, there are a couple other settings you can edit to keep your PHP application secure. Let's take a look at the checklist below:
After configuring those settings properly, there are a couple other settings you can edit to keep your PHP application secure. Let's take a look at the checklist below:
- expose_php = Off
- This restricts the disclosure of PHP version from being sent in HTTP Headers. When enabled, expose_php tells everyone that PHP is installed on that specific server or system, which includes the PHP version within the HTTP header, e.g (Powered by: PHP/8.1.2). You can do this for any system and works well if you are using nginx.
- allow_url_include=Off
- Setting this to off prevents remote code execution attacks.
- display_errors = Off
- This displays whether errors should be printed on the screen to everyone visiting the site. This should be disabled as a best security practice.
- session.cookie_httponly = 1
- Setting this to 1 disables access to cookies via Javascript APIs but use this with caution as you could break something
- session.use_strict_mode = 1
- Setting this to 1 prevents session fixation attacks
- session.cookie_secure = 1
- This requires cookies to strictly transmitted over HTTPS only
- session.cookie_samesite = Strict
- Setting this to strict prevents cross-origin attacks
- session.use_trans_sid = 0
- This is not needed so set it to zero
- session.sid_length = 128
- Here, we are setting the length of the session string which prevents brute force attacks
- session.sid_bits_per_character = 6
- This increases the randomness of the session string which also prevents brute force attack
- file_uploads=off
- Here, we are disabling file uploads. If anyone needs to upload files, you can set a limit on the size of the files by doing upload_max_filesize = 1M
3. Use up-to-date code dependencies and third-party components, and update your web server!
Update your web server to implement up-to-date code dependencies and third-party components, so your cloud security frameworks utilize newly obtained knowledge to prevent exploits in cybersecurity vulnerabilities. If you use Apache Web Server, keep it updated, turn on error logging, add firewalls, set HTTP limits, and only stay active modules. Install mod_evasive, which will maintain running servers even when attacked. An SSL certificate can provide data and network security in online communication.
4. Do not store passwords using reversible encryption
Avoid storing passwords with reversible encryption that attackers can easily crack and decrypt for attackers to spy on and track your activities. Hackers can also enumerate all other passwords if you have a static decryption key. Hash passwords with algorithms like bcrypt, AES, Open SSL, and Argon2. These options are less vulnerable to attacks in network security, making them better password-storing options that will protect your server from data theft issues.
5. Don’t rely on cookies for security
Encrypt cookies before relying on them for security since cookies cannot protect login credentials and sensitive data alone. Use network security toolkits like Halite (by Libsodium), OpenSSL, or AES 256-bit with CBC mode encryption to prevent hacking.
6. Validate user input
Only process PHP codes once you validate the user input so PHPs can verify forms, URL parameters, and JSON payloads with filter_var() options like the one below. Utilize this coding to prevent Cross-Site Scripting (XSS) and other malicious attacks.
|
function is_valid_email($email = "") |
|
|
{ |
|
|
return filter_var(trim($email), FILTER_VALIDATE_EMAIL); |
|
|
} |
7. Perform regular security audits
Perform web and cloud security audits to identify web application security vulnerabilities so you can utilize security patching to fix them before an attack. Such audits can improve response times and provide more reliable application performances. These web and cloud security scanners can check for Cross-Site Scripting Vulnerabilities (XSS), Cross-Site Request Forgery Vulnerabilities (CSRF), SQL Injections, PHP Code Injection, Cookie Denial of Service Attacks, and Timing Attacks.
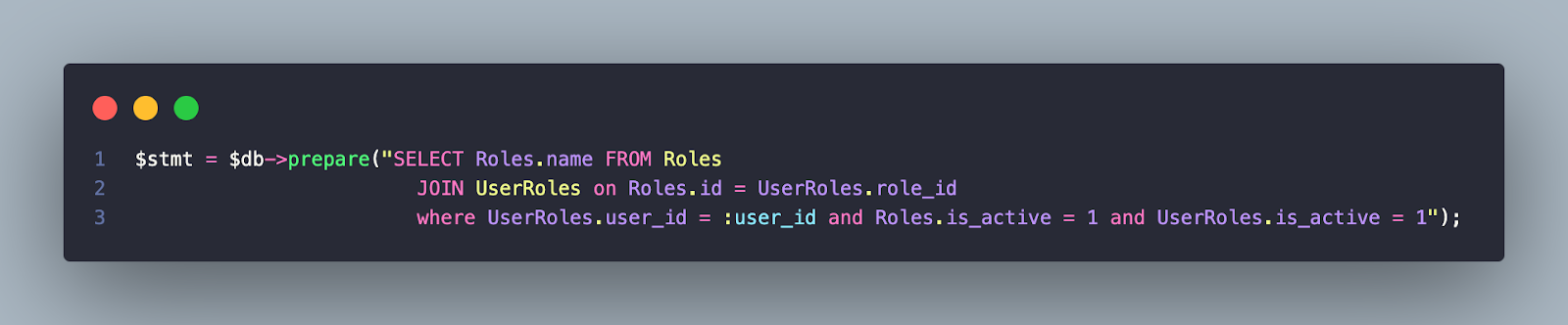
8. Use PHP Libraries
Use PHP Libraries so your developers can secure applications better for functionality. Consider the following coding options for preparing your server.
Final Thoughts on PHP Security
Having a PHP in your server is vital to ensuring robust data and network security. Threat actors like to take advantage of exploits in cybersecurity left behind by poor configurations, so be sure to follow the best php cybersecurity practices we discussed here so you can improve your security posture. Regularly perform web and cloud security audits to identify PHP security issues before they become a substantial risk.
Incorporating AI-driven security strategies are becoming increasingly important in the proactive identification and mitigation of sophisticated cyber threats, which PHP applications may also need to consider in their ever-evolving security protocols.





















