Fileless Malware on Linux: Anatomy of an Attack

Recent years have demonstrated that Windows users are not the only ones who should be concerned about malware. Linux is becoming an increasingly popular target among malware operators due to the growing popularity of the open-source OS and the high-value devices it powers worldwide. Security researchers from AT&T Alien Labs are now warning that “cyber gangs have started infecting Linux machines via a fileless malware installation technique that until recently was more commonly used against Windows-based systems”.
So what exactly is fileless malware and how does a fileless malware attack on Linux work? This article will provide you with answers to these questions by honing in on the anatomy of a Linux fileless malware attack - equipping you with the knowledge necessary to secure your systems and your data against this stealthy and malicious threat. Let’s begin by exploring the concept of fileless malware.
Fileless Malware 101
Unlike traditional malware which leverages executive files to infect systems, fileless malware does not rely on files to accomplish this - as its name suggests. Rather, this stealthy new type of malware infiltrates a server’s random-access memory (RAM) and exploits existing, trusted software and applications known as LOLBins to install and run malicious code on target systems. This strategy of essentially turning systems against themselves is referred to as “living off the land”. Malicious code downloaded on the target system is often used to encrypt and exfiltrate sensitive data, and transfer it directly into the hands of the attacker. Fileless malware attacks leave no trace on the systems they infect, as all malicious activity is performed directly in RAM and no files are written to the hard drive. This type of attack is considered an Advanced Volatile Threat (AVT) - after the affected system reboots all malicious code present on it disappears, but damage has already been done to the impacted server.
Because fileless malware does not leverage executable files to infect systems and therefore has no signature, it is able to evade the detection of signature-based antivirus software and many traditional security solutions.
How Does a Fileless Malware Attack on Linux Work?
Fileless malware attacks targeting Linux systems are carried out in a series of clearly-defined steps, beginning with infection via the exploitation of a vulnerability and ending with the compromise of a server and the data it houses. Let’s take a closer look at how fileless malware attacks on Linux systems work, broken down step-by-step, to help you better understand this growing threat to your systems and your data.
Step 1: Infection via Exploitation of a Vulnerability
Whereas fileless malware infects Windows systems via a malicious link delivered in a phishing email, fileless malware infects Linux systems by exploiting a vulnerability such as a flaw in a network protocol or in a browser’s Flash plugin. For instance, TeamTNT’s infamous Ezuri Golang malware exploits misconfigured Docker instances and exposed APIs to turn vulnerable systems into DDoS bots and cryptominers.
Step 2: Modification of a Linux Process
Once it has gained access to the target system through the exploitation of an unpatched security bug, the malware modifies and crashes a running Linux process using the ptrace() system call. This system call is commonly used by debuggers to inspect and manage the internal state of the target process, and is useful in software development.
Step 3: Insertion of Malicious Code into Memory
Once the malware has crashed a running process using ptrace(), it is able to cause the process to insert malicious code into memory without writing to the disk. This is frequently accomplished by exploiting a buffer overflow, or a situation in which a program, while writing data to a buffer, or an area of memory, overruns a buffer’s boundary and overwrites adjacent memory locations.
Step 4: Execution of Malicious Code = System Compromise
Most installed Linux distributions have pre-installed software, which usually has programming language interpreters such as Python, Perl, С Compiler and PHP. Fileless malware exploits these interpreters to execute the malicious code it has inserted into the memory of the target system. By placing malicious code in /dev/shm or/run/shm directory, it is possible to run the file directly in the RAM. Attacks such as those leveraging the Ezuri encryption tool, which use system calls such as memfd_create() to create an anonymous
file in the RAM that can be run, have gained popularity recently.
Once the malicious code is executed, the attacker has successfully compromised the target system. He or she is now capable of performing an array of malicious actions such as damaging the impacted server, stealing sensitive data and encrypting critical files on the system.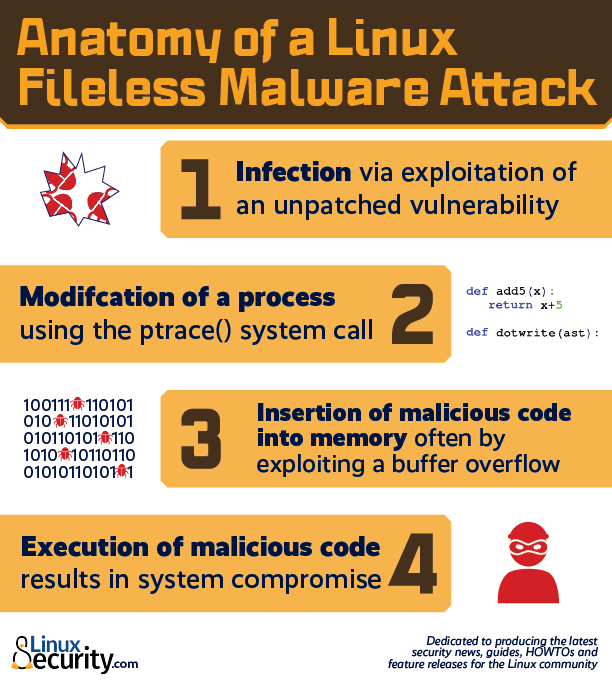
How Can I Protect Against Fileless Malware?
Securing a Linux system against fileless malware and other sophisticated modern threats requires a proactive, layered security strategy. The majority of attacks on Linux systems can be attributed to misconfigurations and poor administration, making it essential that administratorsremain vigilant about testing and verifying the security of their servers. In addition, we recommend that administrators implement these security best practices to protect against filelessmalware and other dangerous exploits:
- Make sure that all software and patches are up-to-date.
- Uninstall applications that are not being used and disable unnecessary services and program features for all necessary applications.
- Restrict admin privileges - only grant the privileges that are necessary for a user to do his or her job.
- Monitor network traffic and check activity logs frequently.
- In the event that an infection does occur, change passwords immediately once you become aware of the infection and again after disinfection.
- Implement adaptive security solutions capable of detecting malicious code – not just on the file system, but also in the RAM.
The Bottom Line
Fileless malware is a growing concern for Linux administrators. Linux is considered a very secure OS by design - and rightfully so. With its robust privilege system and the “many eyes” of the open-source community scrutinizing the increasingly popular OS’s code for security vulnerabilities, Linux users are generally much safer than their Windows-using counterparts. That being said, sound administration and the implementation of security best practices can help prevent fileless malware attacks and other dangerous modern exploits that threaten Linux systems.





















