
As we transition to an increasingly digital society, privacy and security, have become areas of central concern – not a day goes by that we aren’t bombarded with security news headlines about hacks, breaches, and the increasingly common and worrisome practice of storing and monitoring sensitive personal information, often without users’ consent.
Luckily for us Linux users, the general consensus among experts is that Linux is a highly secure OS - arguably the most secure OS. While all Linux “distros” - or distributed versions of Linux software - are secure by design, certain distros go above and beyond when protecting users’ privacy and security. We’ve compiled a list of our favorite specialized secure Linux distros and spoken with some of their lead developers to find out what makes these distros so great. This article will help you evaluate your options and select the distro that best meets your needs.
The State of Linux Security: A Brief Overview
Regarding security, Linux users are undoubtedly faring far better than their Windows- or Mac-using counterparts. Linux offers inherent security advantages over proprietary OSes due to its diversity, flexibility, transparency of its open-source code, and strict user privilege model. Linux source code undergoes constant, thorough review by a vibrant global community, and as a result of this scrutiny, Linux security vulnerabilities are identified and remedied very rapidly. In contrast, proprietary source code is hidden from outsiders, and users depend upon vendors to find, fix, and disclose vulnerabilities.
Along with its secure open-source roots, the diversity possible within Linux environments and the high level of configurability and control that Linux provides sysadmins with features built into the kernel, such as SELinux and AppArmor, also help defend against attacks. In this sense, Linux is in many ways secure by design.
Although attacks targeting Linux systems are on the rise, Linux is still a relatively unpopular target among malware operators and malicious hackers due to its small user base. Most malware still preys on Windows users, with 83% of all malware attacks in 2020 targeting Windows systems.
Why Choose A Specialized Secure Linux Distro?
While moving from a proprietary OS to a regular Linux distro such as Ubuntu, Fedora, or Debian can significantly boost your privacy and security online, there is also a wide selection of specialized secure Linux distros available for users with serious privacy needs such as pen-testers and ethical hackers whose work requires that they conceal their identity online. All of these secure Linux distros have an intense focus on providing users with maximum security, privacy, and anonymity online, and many of them incorporate Tor technologies and offer an impressive selection of hacking, pen-testing, and digital forensics tools. As you can imagine, these characteristics and resources are invaluable when assessing an organization's security infrastructure or conducting a security audit.
Each distro offers unique features and benefits designed to meet users’ varying requirements and priorities. However, these benefits come with some tradeoffs. The most popular programs and OSes typically have the weakest privacy protections but are compatible with most websites and offer the most support. While certain secure Linux distros are relatively mainstream and user-friendly, others have a steep learning curve, especially for less tech-savvy users.
Our Top Secure Linux Distros for Security, Privacy & Anonymity
1. Qubes OS
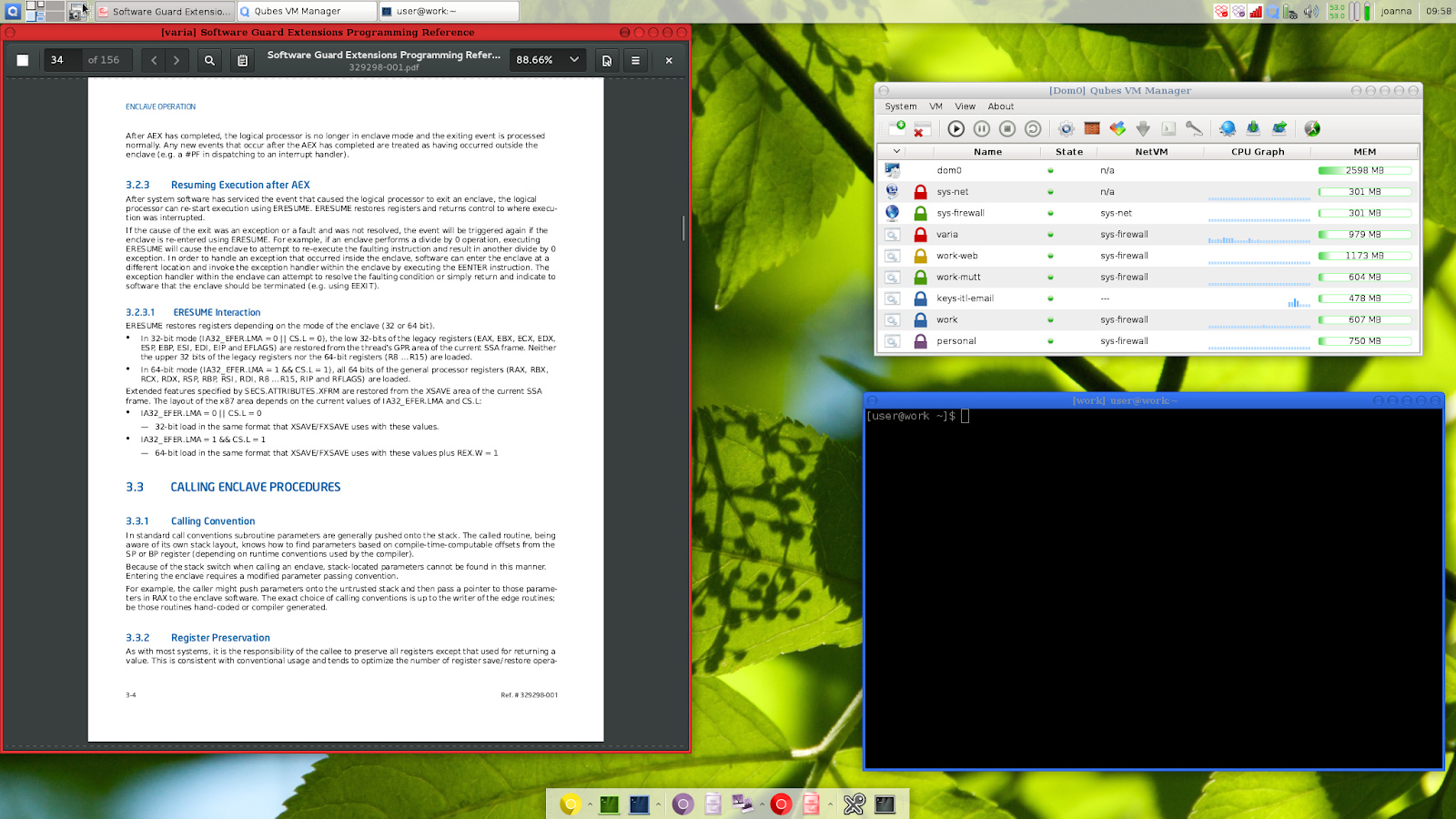
Qubes OS is an ideal choice for users looking to mitigate risk by compartmentalizing their digital lives. A key feature of this operating system is the confinement of high-risk applications to separate virtual machines. Multiple virtual machines - or “Qubes” - are used to organize and separate systems around ‘work’, ‘personal’, ‘Internet’ and so on. These Qubes, conveniently color-coded to help users differentiate them, are highly secure and can offer privacy advocates peace of mind in an increasingly invasive digital environment. As a result of this compartmentalization, if you download malware to your work machine, your personal files won’t be affected, and vice versa.
Integration of various Qubes is provided by the Application Viewer, which creates an illusion for the user that all system applications execute natively on the desktop - when, in reality, they are hosted in isolation in separate Qubes. The Dom0 domain manager, which manages the virtual disks of all other VMs, is isolated from the network to prevent attacks from an infected VM.
In a conversation with the LinuxSecurity editors, Qubes OS Community Manager Andrew David Wong elaborated, “Rather than attempting to fix all of the security bugs in software, Qubes assumes that all software is buggy and compartmentalizes it accordingly, so that when flaws are inevitably exploited, the damage is contained and the user's most valuable data is protected.”
Why We Love Qubes OS:
- Its “Security by Isolation” approach using containers - aka “Qubes” - eliminates the concern of compromised programs.
- These Qubes are integrated into one common desktop environment and color-coded to help users stay organized.
- Sandboxing protects system components.
- Qubes OS offers full disk encryption for maximum file protection.
2. Tails
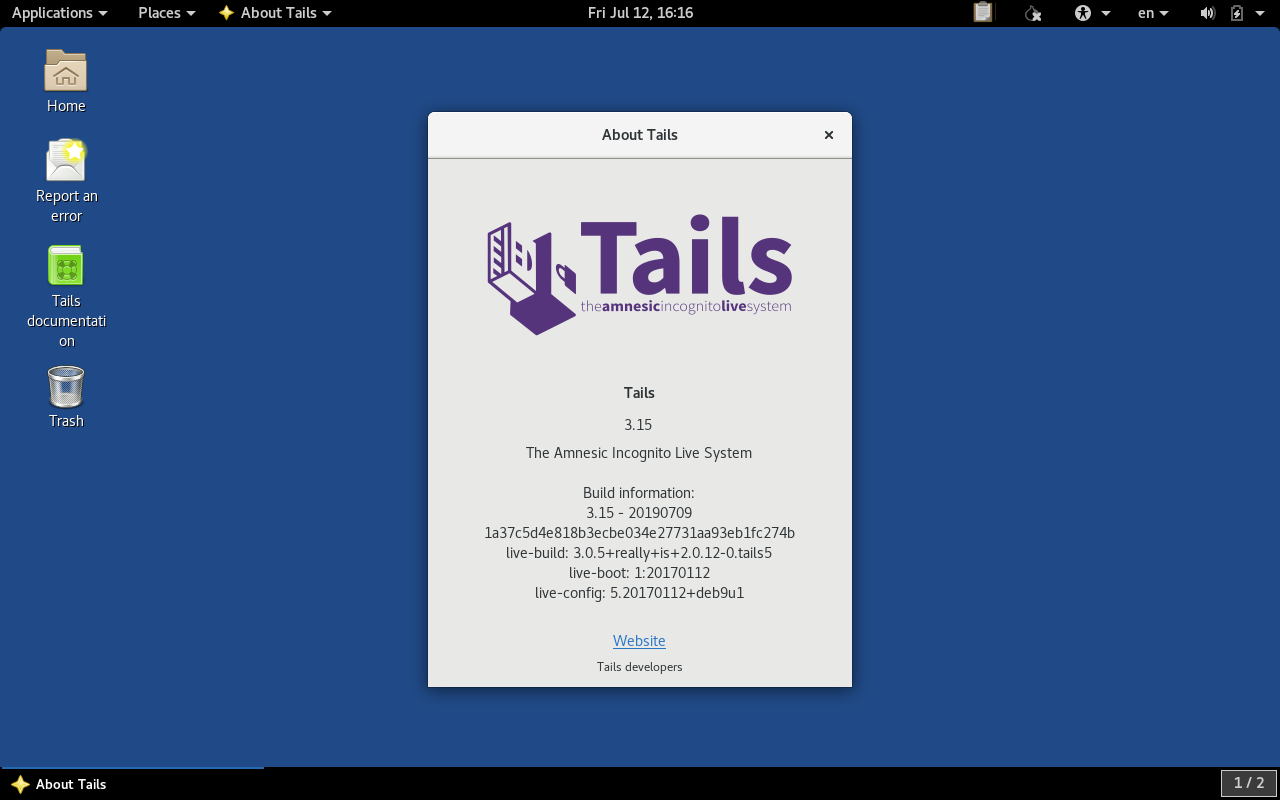
Tails uses the Tor network, a network heralded for its privacy and anonymity benefits, to keep users safe online. All connections run through this network, concealing users’ locations and other private information. Tails has a secure browser, email client, and other secure Internet tools. Tails is the most well-known privacy-focused distro and a popular choice among less tech-savvy security enthusiasts.
A Tails Project contributor explains, “With Tails, anybody can turn any computer into a secure environment free from malware and capable of circumventing censorship.”
On top of Tor's privacy and anti-censorship properties, Tails empowers users worldwide by developing and distributing an integrated and secure operating system that protects users from most surveillance and censorship threats by default. The distro provides a level of security that individual applications cannot achieve because they ultimately depend on the safety of the underlying operating system.
The Tails Project relies heavily on donations and partnerships to maintain its independence and to continue serving the Linux community.
Why We Love Tails:
- Its tight integration with the Tor network ensures anonymity online.
- The web browser is pre-configured for maximum security and includes add-ons like NoScript, Ublock Origin, and HTTPS Everywhere.
- Users get access to Onion Circuits, a valuable tool that allows them to view how their PC traverses through the Tor network.
- Tails comes with the Aircrack-NG wireless network auditing tool.
- The OS is encrypted and designed to run with full functionality on a USB drive.
- The distro features a built-in Bitcoin wallet ideal for users looking to make secure cryptocurrency transactions.
3. Kali Linux
Kali Linux is an industry-standard pen-testing distro. It is one of the most popular distros among pentesters, ethical hackers, and security researchers worldwide and contains hundreds of tools.
A Kali Linux contributor provides some insight into the distro’s history and the benefits it offers users: “Named after a Hindu goddess, Kali has been around for a long time – but it’s still updated weekly, can be run in live mode or installed to a drive, and can also be used on ARM devices like Raspberry Pi.”
Why We Love Kali Linux:
- Kali Linux uses LUKS full-disk encryption to protect sensitive pen-testing data from loss, tampering, and theft.
- This flexible distro offers full customization with live-build.
- Users can automate and customize their Kali Linux installations over the network.
- “Forensics” mode makes this distro perfect for forensics work.
- There’s a Kaili Linux training suite available called Kali Linux Dojo, where users can learn how to customize their own Kali ISO and learn the basics of pentesting. These resources are available on Kali’s website, free of charge. Kali Linux also boasts a paid-for pentesting course that can be taken online, with a 24-hour certification exam. Once you pass this exam, you’re a qualified pentester!
You can learn more about Kali Linux features and settings in this cheat sheet.
4. Parrot OS
Parrot OS can be seen as a fully-portable laboratory for a wide range of cyber security operations from pentesting to reverse engineering and digital forensics - but this Debian-based distro also includes everything you need to secure your data and develop your own software.
Parrot OS is frequently updated and provides users with a wide selection of hardening and sandboxing options. The distro’s tools are designed to be compatible with most devices via containerization technologies such as Docker or Podman. Parrot OS is very lightweight and runs surprisingly fast on all machines - making it a great option for systems with old hardware or limited resources.
Why We Love Parrot OS:
- The distro provides pen-testers and digital forensics experts with the best of both worlds - a state-of-the-art “laboratory” with a full suite of tools and standard privacy and security features.
- Applications that run on Parrot OS are fully sandboxed and protected.
- Parrot OS is fast, lightweight, and compatible with most devices.
5. BlackArch Linux
This popular pen-testing distro hails from Arch Linux and contains over 2,000 hacking tools - allowing you to use whatever you need without downloading new tools. BlackArch Linux offers frequent updates and can be run from a USB stick or CD or installed on your computer.
BlackArch Linux is similar to both Kali Linux and Parrot OS in that it can be burned to an ISO and run as a live system, but is unique in that it does not provide a desktop environment. However, this up-and-coming distro does offer a large selection of preconfigured Window Managers.
Why We Love BlackArch Linux:
- BlackArch Linux offers a large selection of hacking tools and preconfigured Window Managers.
- The distro provides an installer with the ability to build from source.
- Users can install tools individually or in groups with the modular package feature.

6. Whonix
Sometimes, using a live OS can be inconvenient – you have to restart your machine each time you want to use it, which is tedious and time-consuming. Installing an OS on your HD, however, you risk the OS being compromised. Whonix offers a solution to this predicament – a virtual machine that works inside the free program Virtualbox and aims to provide security, privacy, and anonymity on the Internet.
This Debian-based distro operates in two parts – the first part, the Gateway, routes all connections to the Tor network. The second part, the Workstation, runs user applications and can directly communicate only with the Gateway. The Workstation VM can only “see” IP addresses on the Internal LAN, which are identical in every Whonix installation. Therefore, user applications have no knowledge of the user’s actual IP address, nor do they have access to any information about the physical hardware of the machine that the OS is running on. This split design allows the user to remain completely anonymous and mitigates the risk of DNS leaks, which reveal private information such as your web browsing history.
Whonix has recently added an amnesic live mode that “forgets” users’ activities - not leaving traces on disk. The distro is currently working to create a unified desktop experience. Whonix developer Patrick Schleizer explains, “Our upcoming Whonix-Host extends many of our usability and hardening features to the entire desktop.”
Whonix encourages users to provide feedback on their experience and sincerely appreciates donations and contributions to support the project’s ongoing efforts.
Why We Love Whonix:
- Whonix comes with the Tor Browser and the Tox privacy instant messenger application - ensuring fully anonymous web browsing and instant messaging.
- The OS employs an innovative Host/Guest design to conceal users’ identities behind the anonymous proxy and prevent IP and DNS leaks.
- The distro features pre-setup Mozilla Thunderbird PGP email.
- Linux Kernel Runtime Guard (LKRG), a kernel module that performs runtime integrity checking of the Linux kernel to detect security vulnerabilities and exploits, can be easily installed on Whonix.
Final Thoughts on Choosing a Secure Linux Distro
A selection of excellent specialized secure Linux distros is available to pen testers, software developers, security researchers, and users with a heightened concern for their security and privacy online. Choosing the best Linux distro for your privacy needs is a balancing act - each distro offers a different balance of privacy and convenience.
Based on your specific requirements and concerns, it is likely that one (or many!) of the distros profiled above could be a great fit for you, offering the tools and capabilities you are looking for in a distro, coupled with the peace of mind that your system is secure and your privacy is protected online.























