The Three Best Tools You Need to Scan Your Linux System for Malware

Learn about the growing importance of scanning Linux systems for malware, and our favorite tools for doing so.
Why You Need to Protect Your Server against Malware
While Linux Servers are already extremely secure by default, there are extra steps you can and should take if you do have a Linux Server instance running. As with any system, vulnerabilities still exist and can wreak havoc if proper prevention and security best practices are not implemented. Of course, the most well known and most basic security tip people will tell you is to keep up to date with updates and security patches. (As we all should!) However, this will only do so much. Linux being amongst one of the most widely implemented and deployed operating systems makes it an attractive target for cybercriminals trying to steal your information, install malicious files on your system, and even try to run malicious scripts to take control of your system.
Nowadays, there are some people and even organizations who treat security as a secondary measure and sometimes, even treat it as a non-factor. LinuxSecurity values our role in helping you keep your Linux servers safe and secure as much as possible. In order to secure our server along with our data, and furthermore check whether our system has been compromised, we have created a list of the best malware scanners we’ve used over the years that will assist you in checking your system for any malware. This article will explore the security tools used for checking malware along with instructions on how to go about using these tools.
Of course you will be running these tools if you suspect there is malware on your system or if you are looking to prevent malware on your system, however, these tools are also just general security best-practices to audit your servers to further identify areas that could be secured.
What Types of Malware do Users and System Administrators Face Today?
Malware targeting Linux systems has increased tremendously over the past couple years, posing a threat to daily users and an even bigger headache for System Administrators. The different types of malware that Linux users can find themselves facing ranges from viruses and trojans to ransomware, botnets, keyloggers, worms, and even rootkits. System Administrators constantly have to find themselves keeping up with the latest Cyber threats and at times, can even find themselves part of a Zero-day attack if exposed to a malware that exploits unknown entry points into a system.
There are new attacks on the rise such as Cryptojacking and XorDDoS that have become rather troublesome. Cryptojacking involves Cybercriminals gaining unauthorized access of peoples devices to mine for cryptocurrency and these attacks are designed in such a way to be undetectable. An example of this would be the very recent Xbash malware. Xbash is a Python script that targets Linux servers and combines ransomware, mining, and botnet. These scripts contain commands to kill a list of processes. XorDdos, on the other hand, is a Trojan malware specific to Linux that utilizes rootkits and XOR encryption algorithm to carry out ‘SSH brute force’ attacks, and ultimately, use these devices as a botnet. These are just a few of the many types of malware out there that Cyber Criminals can and will use against your systems.
Preventative Measures to Keep Your System Secure
When it really comes down to it, it is better to take preventative measures rather than taking recuperative actions later on down the road. Now although systems cannot be fully “protected” from outside intruders, we can do our best to keep them at bay. Here are some preventative measures you can take beforehand to keep your system safe:
- Update software regularly
- Set up Linux security extensions for controlling and restricting access to data and resources
- Use network segmentation to minimize the reach of a potential ransomware attack
- Adopt a strong password policy
- Set up network monitoring
- Perform vulnerability scans and penetration tests
- Regularly inspect event logs to identify anomalous behavior
- Create system backups and include immutable backups
- Set up IP filtering
- Set up an intrusion detection system
- Set up an intrusion prevention system
- Ensure servers and endpoints are up to date with the latest security patches
Now if you have taken some of the preventative measures above, and some malicious malware still manages to make its way onto your Linux device, let's look at how we can detect malware that's already on our system. We advise you to take a look at this list of malware tools for Linux that we have devised to hopefully combat the up and rising malware attacks.
What If There's Malware? Our Top Choices for Linux Malware Scanning
We recommend these following malware tools to further audit your systems for any traces of malware.
Lynis
Lynis is an open-source security auditing tool for UNIX-based systems. It performs an in-depth security scan and is primarily used to test security defenses and provide insight for further system hardening as well as scanning for general system information, vulnerable software packages, and possible configuration issues. It also scans for security information, installed and available software information, configuration mistakes, security issues, user accounts without a password, wrong file permissions, firewall auditing
Use Case:
- Security auditing
- Compliance testing
- Penetration testing
- Vulnerability detection
- System Hardening
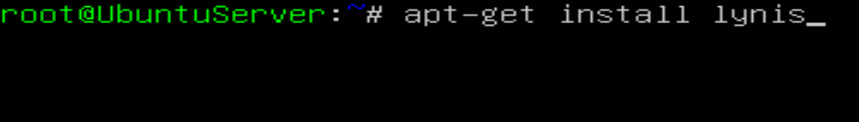
How to install via terminal:
How to check Lynis Commands:
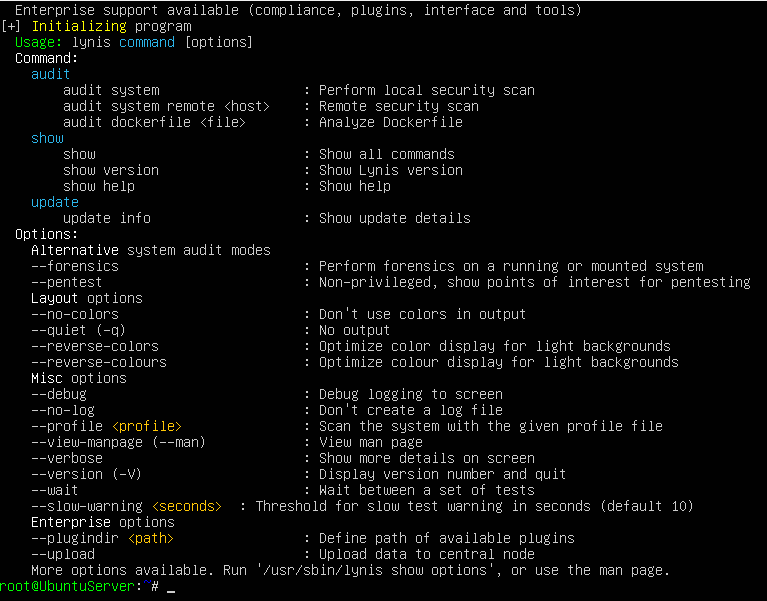
This should output:
Lynis audit Command:
This should output:
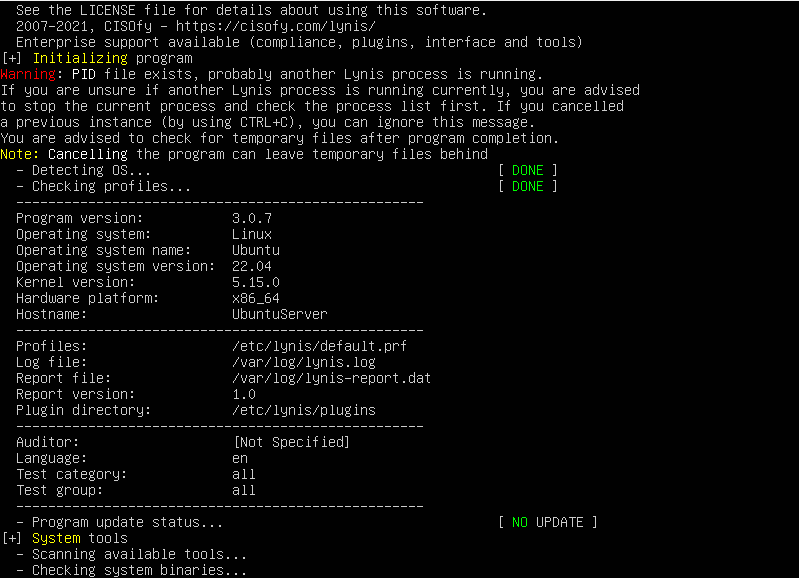
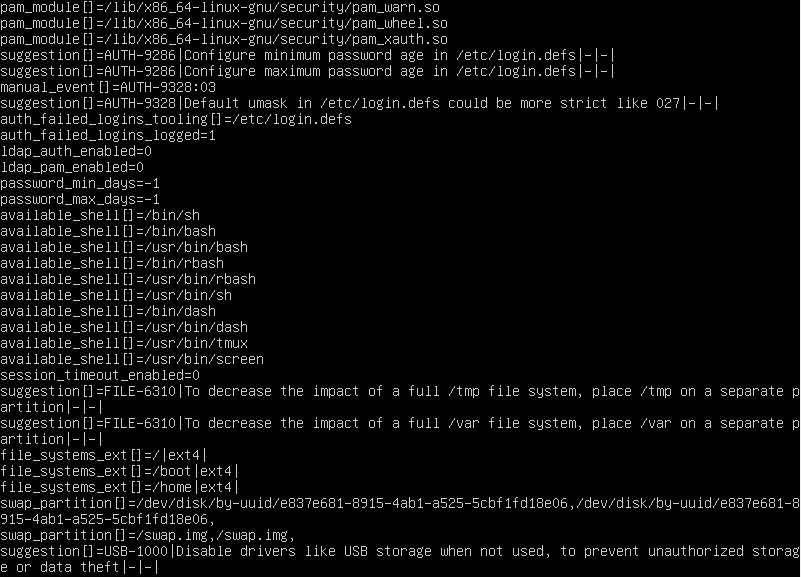
Running the command lynis audit system generates two files: lynis.log and lynis-report.dat. The lynis.log file logs all the tests that were performed during the audit of the system and returns the result of said tests. The lynis-report.dat file contains a report that provides suggestions for strengthening the system. Ultimately, it reveals important information about your system’s security and possible misconfigurations and vulnerabilities. Here is a sample lynis-report.dat file:
Chkrootkit
Rootkits give people the ability to remotely control your computer. Sometimes they can be difficult to detect and are even harder to remove. Chkrootkit is a tool to locally check for signs of a rootkit or simply put, it is basically a shell script that makes use of simple linux commands to check for discrepancies in the System binaries. Chkrootkit can easily identify a trojaned system command while it looks for known signatures.
How to install via terminal:
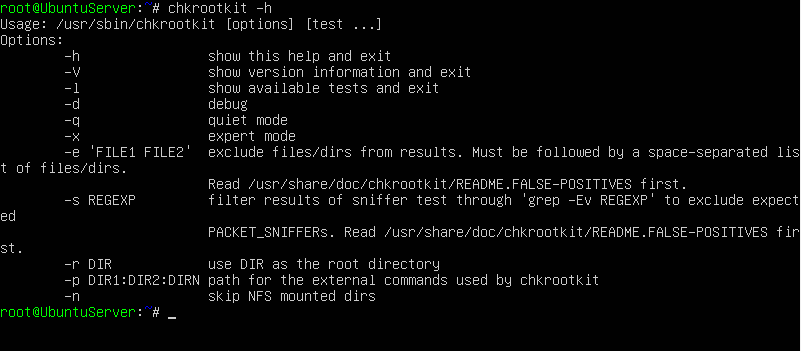
How to check Chkrootkit Commands:
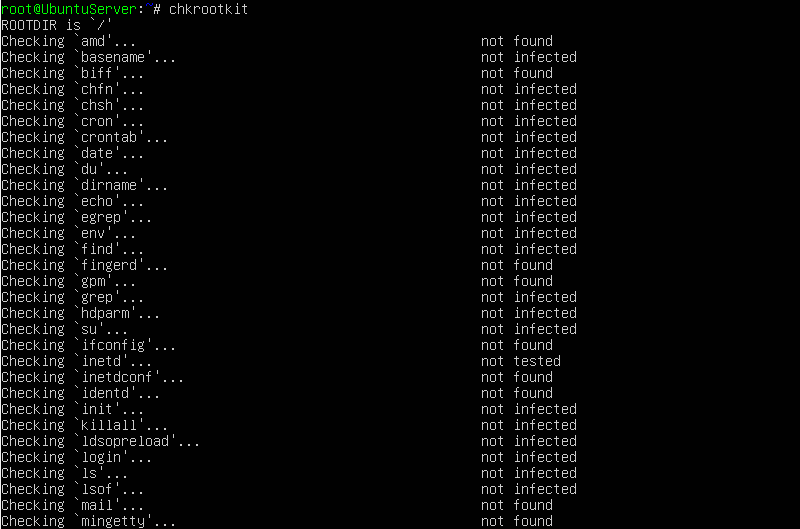
Chkrootkit Running:
Chkrootkit with Grep:
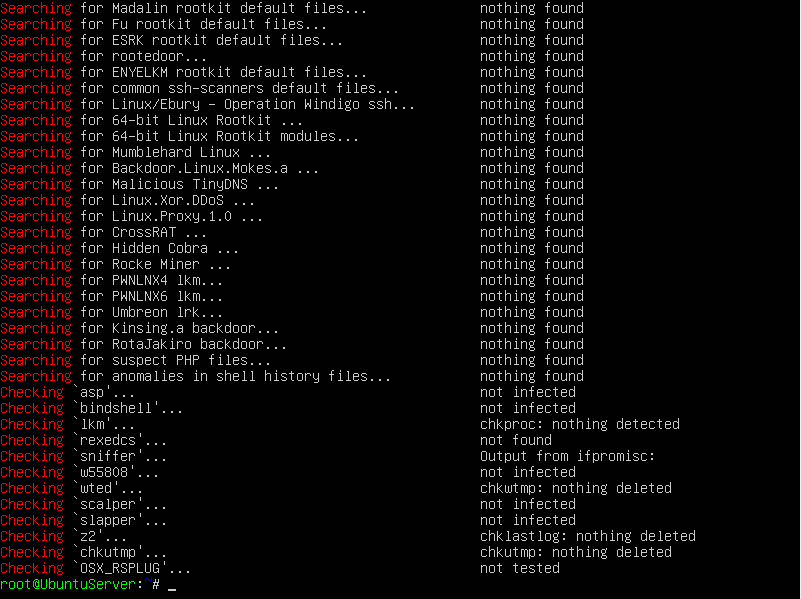
This should output:
These messages are printed by chkrootkit during its tests:
- "INFECTED": the test has identified a command probably modified by a known rootkit;
- "not infected": the test didn't find any known rootkit signature.
- "not tested": the test was not performed -- this could happen in
- "nothing found": the command to be tested is not available;
- "Vulnerable but disabled": the command is infected but not in use. (not running or commented in inetd.conf)
Chkrootkit in Expert mode:
This should output:
Chkrootkit in Expert mode with Grep:
This should output:
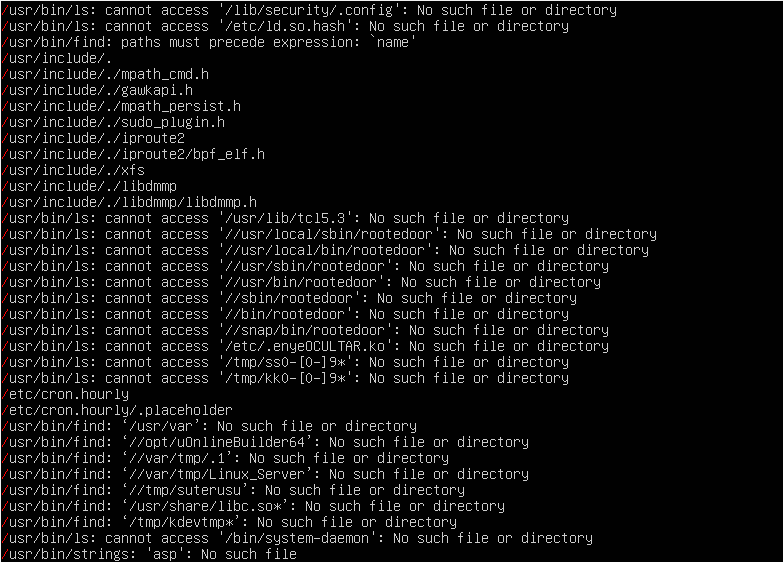
The parameters that we specified in the chkrootkit -x | egrep ‘^/’ command will run chkrootkit in expert mode and specifies pathname strings in system commands and this helps when looking for suspicious strings in the system's binaries. Since chkrootkit's set of known signatures is fixed, this parameter helps to extend chkrootkit's abilities.
Rootkits pose a growing threat for the future. Chkrootkit is an Intrusion Detection System that helps to prevent potential harm that can be caused due to the existence of loopholes and possible entry points in your system and furthermore, helps in the remediation process if your system has been compromised.
Linux Malware Detect
Linux Malware Detect is a free and open source malware scanner for Linux that is designed to use threat data from network intrusion detection systems and create signatures of malware actively being used in attacks.
How to install via terminal:
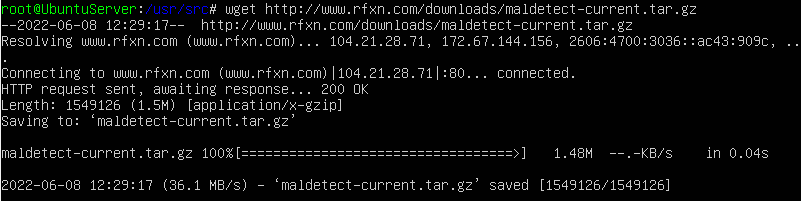
Linux Malware Detect has to be downloaded from the R-fx Networks – Linux Software & Blog website. We use the command wget rfxn to get the download and save it in our current working directory.
How to extract the download:
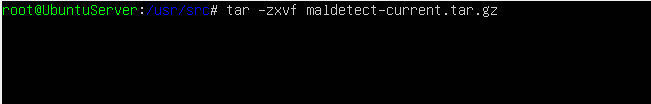
We use the tar -zxvf maldetect-current.tar.gz command to extract the tar file.
Change to maldetect-*version directory:
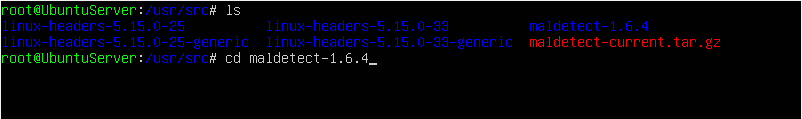
If we use the ls command to check the contents of our directory after extracting the tar file, we see that a new folder has been created called “maldetect-1.6.4”. We want to change to this directory using the command cd maldetect-1.6.4. Depending on the time you read this tutorial, there might be a different version of maldetect released so just make sure you pay attention to the directory name as it is bound to change with new releases.
Run the Install Script:
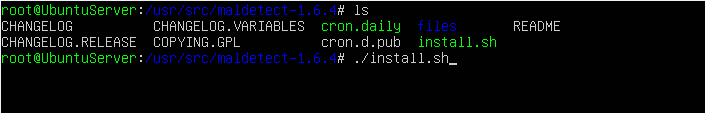
Using the ls command, we check the contents of our “maldet” directory that was created after extracting the file. We want to run the script called install.sh in this directory to install LMD. Use the command ./install.sh to run the installation script or run the command sh /path/to/file/install.sh depending on where your installation script is.
Doing this should output:
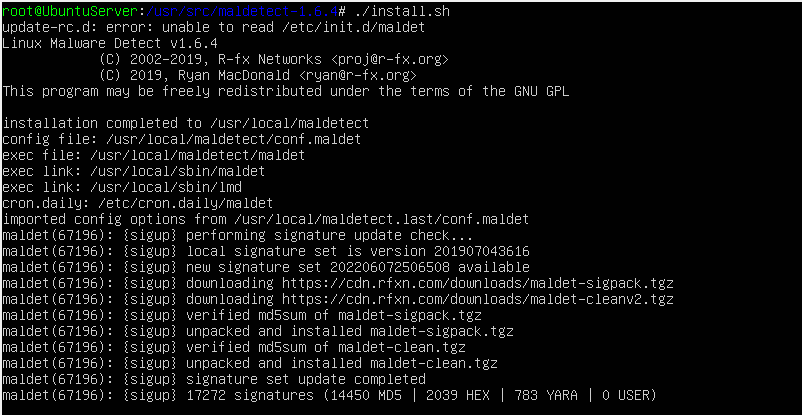
After installation, let’s edit the configuration file:
Using the vi /usr/local/maldetect/conf.maldet command, we can update the configuration file of maldet to edit some settings.
Email Alerts:
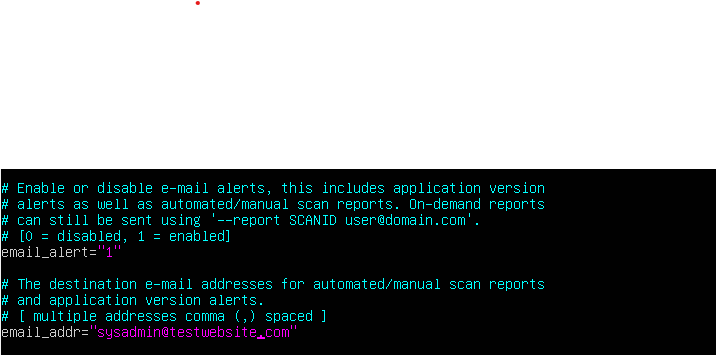
Initially, when you first open the conf.maldet file, you will see that email_alert will be set to 0. If you would like to receive email notifications of the results when automated scans, set this value equal to 1. Underneath, you see a variable called email_addr. As the file states, this is the desired email to where you want your notifications sent. For testing purposes, I've used a “temp” email.
ClamAV configuration:
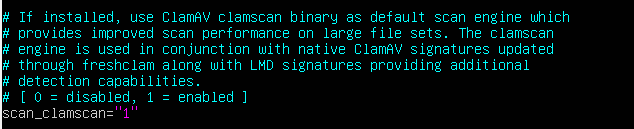
Initially, scan_clamscan will be set to 1. We want to leave it this way to enable clamav and LMD to work together to ultimately provide better performance when scanning. For Reference, ClamAV is an open source antivirus engine for detecting trojans, viruses, malware & other malicious threats.
Maldet commands 
Lets run a maldet command!
maldet -a /var/log will scan the entire directory of /var/log.
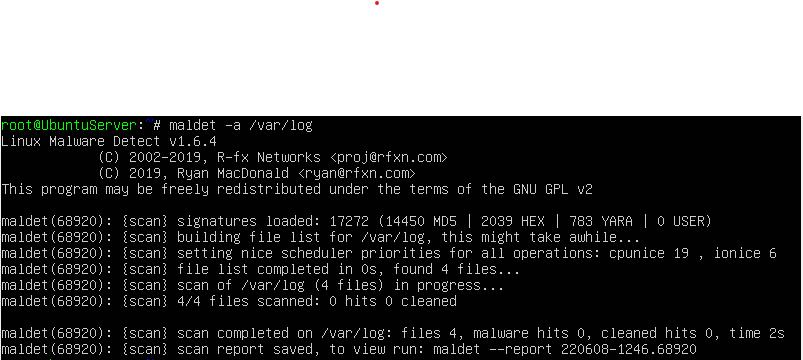
After running, this is what will be outputted: 
After running the command, this is what will be outputted on the screen. If you had email settings setup properly, you should have received an email. If not, let's take a look at how you can view a maldet report. At the bottom of the screen, you can see the output “scan report saved, to view run: maldet –report 220608-1246.68920”. The report name will vary from user to user, this is just my report name. So let's enter that command and see what we get below:
 Maldet Report:
Maldet Report:
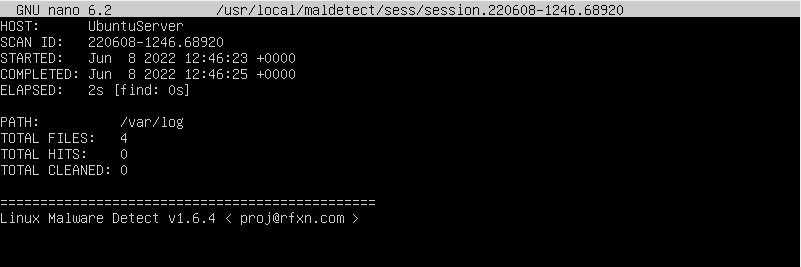
After opening the file, this is the report we are greeted with.You can see it scanned 4 files and there were 0 hits and 0 files cleaned. This means that no files were infected and it didn’t have to clean up anything.
Why These Three Tools?
There are many free, open-source malware detection tools available, however, since each users and/or System Administrators use case is different, we wanted to provide a list of tools that can be used for different purposes. Users and System Administrators alike can pick and choose the right tool for their current use case and install it via the command line or their respective interfaces.
Our Thoughts
As Cyber Criminals become more advanced with their scripts and as cyberthreats are on the rise, we are at a point in time where we cannot afford to have an unsecure system. There are roughly 2200 reported malware attacks each day, not accounting for the ones that go unreported, and it could be prevented with the proper measures. Using the tools above is the first initial step into keeping your server and ultimately, your systems secure. However, you should not just stop at that. Follow along with us as we continue to explore how you can further secure your linux servers and systems. To wrap this all up, we hope you found this article useful. Also be sure to check out our 'Complete Guide to Protecting a Linux Server from Hackers' for more tips and advice on securing Linux.